At re:Invent 2017 Amazon Web Services introduced Amazon GuardDuty, a managed threat detection service that provides an accurate and easy way to continuously monitor for malicious or unauthorized behavior, helping to protect your AWS accounts and workloads. Amazon GuardDuty gives users the ability to monitor one or multiple AWS accounts for unusual and unexpected behavior. This is accomplished by analysing and monitoring existing logs, such as VPC Flow Logs, CloudTrail Event Logs and DNS Logs. Additionally, Amazon GuardDuty processes data from multiple sources, focusing on threat detection by searching for anomalies and known malicious IP addresses and URLs.
Amazon GuardDuty was specifically developed and optimized for the cloud. AWS Security, in partnership with industry-leading third-party security partners, have developed a constantly increasing database of possible vulnerabilities, along with the patterns that each one presents. By using machine learning, this tool can proactively identify possible threats in your whole infrastructure and classify them in their respective severity level.
With that in mind, you are able to create a plethora of custom rules, along with your own base of known malicious IPs. Amazon GuardDuty offers CloudWatch Events, CLI tools, and HTTPS APIs to assist you in creating your own custom automated functions to handle all alerted threats.
To help you to determine the action you want to take for each alert, GuardDuty provides three levels of severity which we will take a deeper look at in just a moment
- Low severity: indicates threats that have already been removed or blocked before compromising any resource.
- Medium severity: indicates suspicious activity, such as an increase in traffic specifically directed to, for example, bitcoin related domains, indicating cryptocurrency mining.
- High severity: indicates a resource that is fully compromised and is constantly being used for unintended purposes.
Testing Results
Low Severity
For our first test, we wanted to keep things simple by invoking a low severity response from Amazon GuardDuty. In order to do this, we launched an EC2 instance with SSH port 22 open to the world, which is typically used to securely login and transfer files. After setting up the vulnerable environment, we then probed that EC2 instance using a proxy server running ProxyChains on Kali Linux from an unusual source IP address.
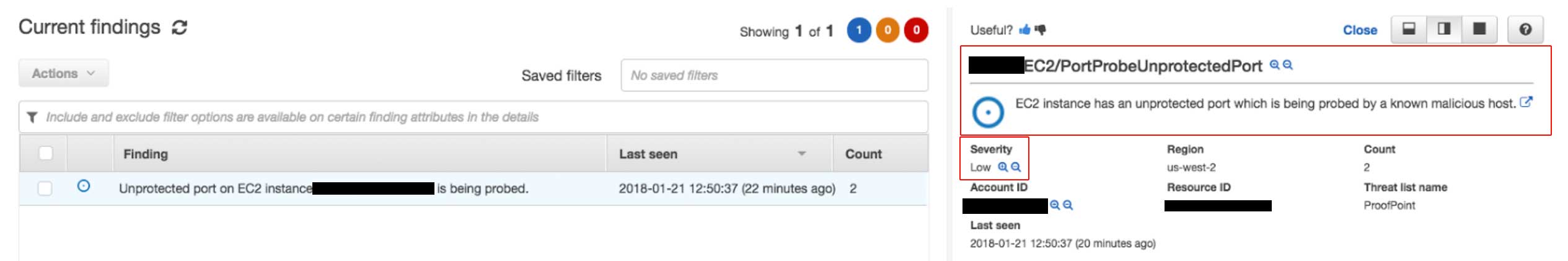
In the image above, you will see that Amazon GuardDuty results immediately detected a low severity threat and provided a description of the event. In the description you will see information regarding which resources were affected, the actor IP address/location, how many times it occurred, along with the time and date of the detected threat.
Medium severity
In the example below, we made some API calls to our AWS account using Kali Linux, which is a distribution commonly used by attackers, pen testers and security experts to identify weaknesses to gain unauthorized access to your environment.
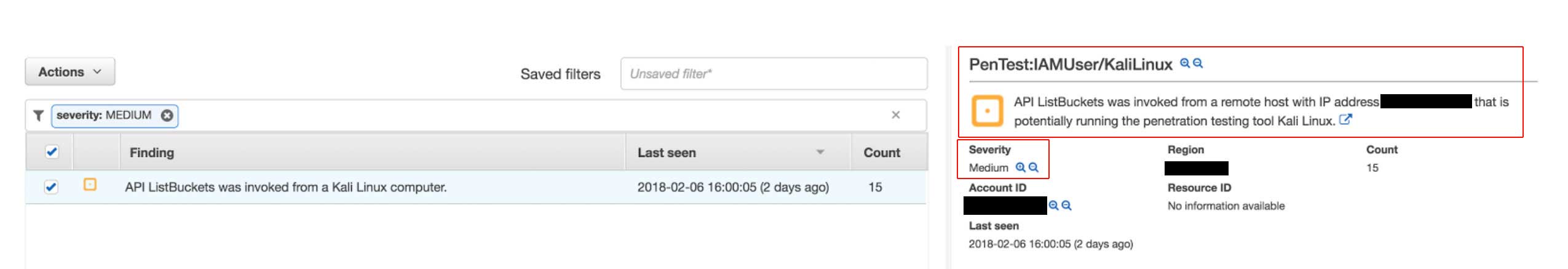
As you can see, GuardDuty detected that an API call was invoked from a Kali Linux computer, indicating that your credentials might be compromised.
High severity
What if someone gained access to one of your instances to perform a malicious activity such as a brute force attack or port scan? In the example below we used one of the EC2 instances in our account to perform a SSH brute force attack against one of our test servers.
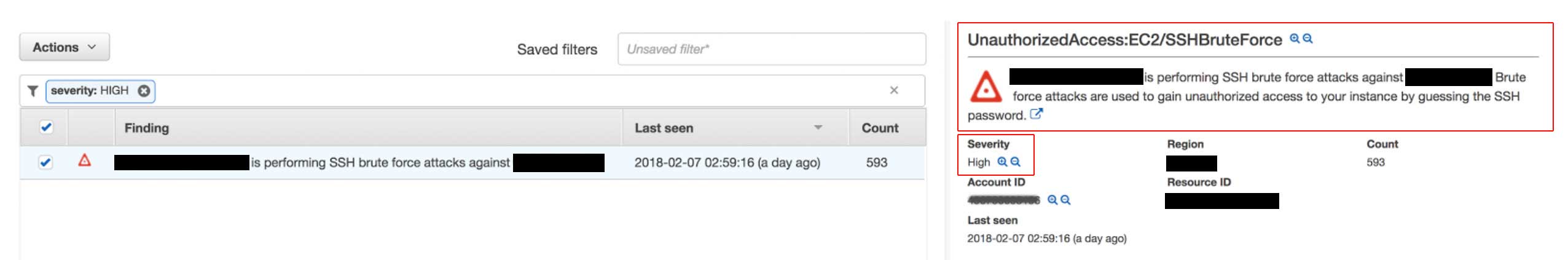
This is considered a high severity issue as it means your instance is already compromised. There are several types of attacks which are constantly being updated by AWS and their security partners. You can find the complete list here.
Pricing
AWS provides a free full access 30 day trial of the service upon the first activation so you can see if it’s a good fit for you. To estimate the costs after that, Amazon GuardDuty generates an estimated price for how much you would have spent without the free trial.
The pricing is based on the amount of analysis of your AWS log data. VPC Flow Logs and DNS Logs will be charged per GB/month and the CloudTrail Event Logs will be charged per 1,000,000 events/month. Even though pricing can differ from region to region, in general it consists of the following:
VPC Flow Log and DNS Log Analysis

To avoid unnecessary expenses, GuardDuty is constantly analysing your infrastructure, knowing exactly the required amount of detection capacity for each specific moment. In other words, you only get charged for the capacity you use, when you use it.
Getting Started
Amazon GuardDuty can be enabled with just a few clicks in the AWS Management console. Once enabled, the service immediately starts analyzing billions of events from AWS CloudTrail, Amazon VPC Flow Logs, and DNS logs.
The service is very easy to enable within your account. Simply click “Enable GuardDuty” within the service dashboard in the AWS management console:
Once enabled, the service will immediately begin the analysis process. Any findings will be displayed on the dashboard, categorized by the appropriate severity level. The details about each finding gives you valuable insight allowing you to dig deeper into the potential issue.
If you want to monitor additional resources, such as DNS and VPC Flow logs, you will need to create a VPC Flow Log for the desired resource, which can be from a specific network interface or the whole VPC, and configure Query Logging for your domain on Route53.
Conclusion
After diving into the new Amazon GuardDuty threat detection services, we’re really happy with a lot of the functionality. It’s easy to install, has deep integration with a large number of AWS services, uses machine learning to detect threats (which is pretty awesome), and it’s simple user interface makes it quick to diagnose security vulnerabilities by users of any skill level.
Currently, this service is exclusively available to AWS environments, which means you can’t take advantage of their machine learning threat detection on any other cloud platform. It would be really nice to see AWS extend this functionality outside of AWS. With that in mind, we think Amazon GuardDuty makes an excellent addition to AWS’s suite of services and we’re looking forward to implementing it every chance we get.
FAQ
- How does Amazon GuardDuty integrate with other AWS security services to provide a layered security architecture?
Amazon GuardDuty integrates seamlessly with other AWS security services, such as AWS Security Hub, AWS CloudTrail, and Amazon CloudWatch. This integration allows for a comprehensive security monitoring system where GuardDuty detections can trigger alerts and responses across these services, enhancing the overall security posture by providing layered security measures.
- What specific machine learning models or techniques does GuardDuty use to identify potential threats, and how are these models trained?
Amazon GuardDuty utilizes various machine learning models and anomaly detection techniques to identify and prioritize potential threats. These models are continually trained and updated based on new data, patterns of known threats, and unusual behavior to ensure effective detection of potential security issues without manual intervention.
- Can Amazon GuardDuty be configured to automatically respond to detected threats, and if so, what actions can it take?
- Amazon GuardDuty can be configured to automatically take action against detected threats through AWS Lambda functions. By setting up custom Lambda functions, users can automate responses such as revoking credentials, isolating compromised resources, and sending notifications. This automated response mechanism helps rapidly mitigate threats, reducing the time between detection and response.




